Bug Bounty
Crowdsourcing from a list of the world's top ethical hackers to provide you continuous assessment, for uncovering vulnerabilities before anyone else does.
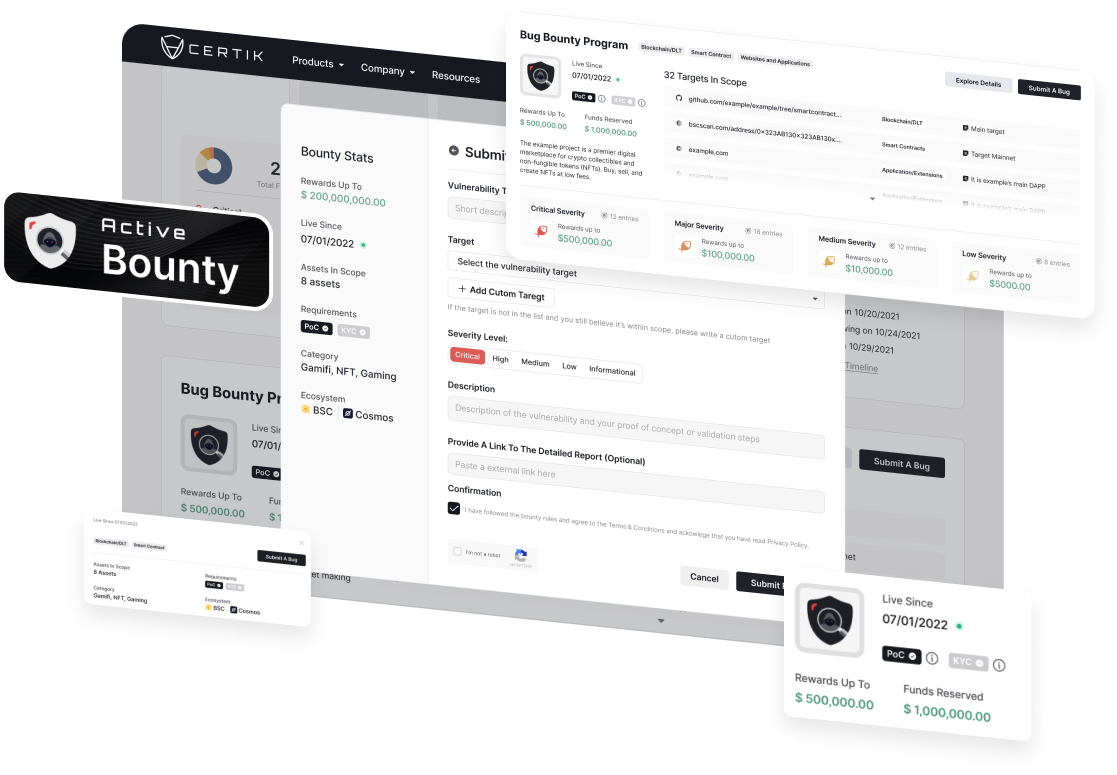
The CertiK Bug Bounty Platform
Combining years of Web3 security experience with a well-established technical community, CertiK’s Bug Bounty is the only Web3 platform providing fully managed end-to-end support with 0% fee on bounty payouts.

Submission Screening and Triage Support
CertiK’s expert security engineers will screen and qualify submissions and work with your team to implement the right fixes.

Community-Focused Ethical Hackers
Tap into our large technical community from the Security Leaderboard to attract leading ethical hackers to your project.

0% Fee on Bounty Payout
Our 0% fee model reduces the payout pressure for projects and allows for white hat hackers receive the full bounty.
Peace of Mind for your project and community
Setting up a bug bounty with CertiK allows projects to utilize the intelligence of ethical hackers to further derisk their code from additional vulnerabilities.

Proactive Defense
White hat ethical hackers who have intuitive knowledge of the latest attacks can realize threats before malicious actors have the opportunity to exploit them.

Crowd Sourced Security
Gain access to a highly-skilled community of ethical hackers that specialize in different areas of vulnerability detection.

Expedited Submission Screening and Triage
Partner with CertiK security engineers who will rapidly review all your inbound bug submissions and help ensure the proper steps taken to fix any issues.

Integration with Skynet Trust Score
Bug bounty remediation of findings is integrated with Skynet and will improve the overall trust score for your project.
The Next Step In Web3 Security
CertiK's bug bounty program offers a trusted platform for projects and ethical hackers to connect.

The Project
1. Get onboarded with a dedicated program manager.
2. Launch your program and activate your bounty badge on certik.com.
3. Receive submissions and pay bounties directly if qualified.

The Leaderboard User
1. Add projects with active bounty badges to your watchlist.
2. Strengthen your technical due diligence capabilities.
3. Evaluate projects with additional security measures.

The Ethical Hacker
1. Sign up to the platform and browse bounties.
2. Review in-scope assets and submit reports.
3. Get paid directly and gain your Web3 white hat reputation.
Working Together to Create a Safer Web3 Ecosystem
Web3, as well as associated Web2 elements of projects are increasingly under attack by malicious actors who seek to take advantage of security vulnerabilities in project code. These adversaries are always "one-step-ahead" of whatever security controls are in place to protect these projects - constantly running reconnaissance and coming up with new attack vectors inside the project’s threat landscape.
